Against all odds, remote work has been gradually accepted, but regardless of how your organization does it, it would be imprudent to overlook the obvious cybersecurity risks presented by remote work. Let’s take a look at the essence of zero-trust security and explore why it has evolved into the standard that organizations of all sizes should adhere to.
It’s hard to believe that it’s already been a few years since circumstances… “encouraged”… so many businesses to suddenly adopt work from home policies. As these circumstances have gradually normalized, many businesses have elected to keep these policies in place, either maintaining fully remote operations or shifting to hybrid operations. However, some notable businesses have taken efforts to roll back remote work capabilities, if not discontinuing them entirely.
“If a craftsman wants to do good work, he must first sharpen his tools.” Like so many of the other quotes attributed to Confucious, this phrase is no less true today, even in the realm of business technology. It should come as no surprise that implementing the right technology for your particular business needs will produce greater results. The real question is how to identify the technology that will contribute to the overall success of your organization.
How much technology does your business use day in and day out? More likely than not, it’s a lot, and we’d bet good money on the fact that you could be doing more to manage it. That said, it’s not always clear how to go about doing it, especially if you don’t have any in-house IT talent to handle this considerable responsibility. With managed services, you can overcome this challenge. Let’s go over what these are and how they work.
Cybersecurity is a complicated beast. Not only do you have to be sure that you’re protected from threats coming from outside your business, there are also a few very real threats that can originate from inside your business, too. Both are critical to prevent, which can be quite effectively accomplished via a zero trust approach to your security.
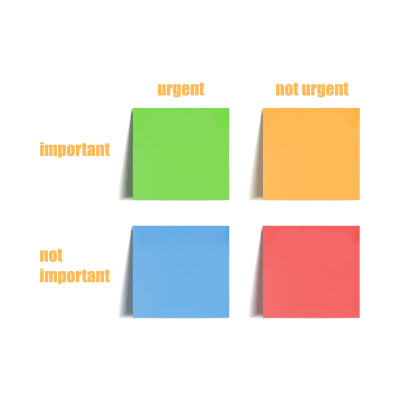
The modern worker has a lot of challenges and one of them is a laundry list of tasks to accomplish. For this reason, it’s best to have a plan for tackling your to-do list. One of the most effective ways to prioritize tasks is through what is called the Eisenhower Matrix. Inspired by a speech given by the former President of the United States and the Supreme Commander of the Allied Expeditionary Force in World War II, the Eisenhower Matrix simplifies complex task lists to make getting through them more effective. Let’s take a look at how it works.
Oh, the afternoon meeting, the woe of many office workers around the world. Sometimes they are fine, but other times, it’s very clear that they are not always an effective use of your time. Despite this, there is still a heavy emphasis on meetings in the workplace, to the point where some employees feel that their time is being wasted and misused as a result—a premise that is supported by surveys and research.
One thing that will always be useful in business and in life is the ability to think critically. You might find that it’s even more helpful when considering decisions related to your IT infrastructure, too. Let’s go over how you can foster these skills within yourself and your employees.
Since it was—somewhat by necessity—implemented by many businesses a few years ago, many of these same businesses have been quick to abandon remote and hybrid approaches to work. If you are considering this return, we implore you to reconsider—in fact, we’d urge you to lean into further expanding the capabilities of remote and hybrid workers.
Wasting money is a major problem regardless of the kind of business you run. Technology can do a lot to stretch your dollars, but it can also be the cause of waste. This week, we thought we’d identify three ways that your business could be wasting significant money on your IT.
- 1
- 2